No, Istio Cannot Break TLS
tl;dr
If your app inside the mesh makes an outbound request to https://thirdparty.com/api/v1, Istio cannot look inside the encrypted traffic.
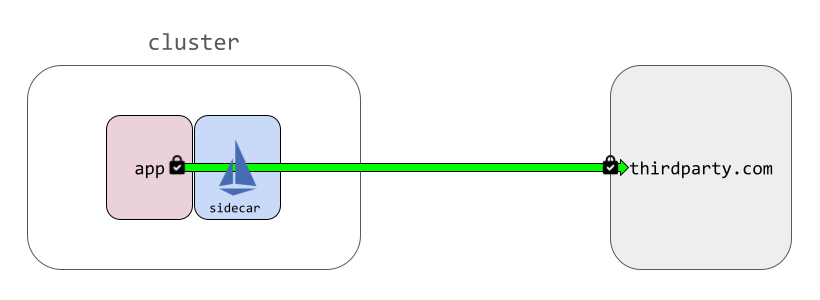
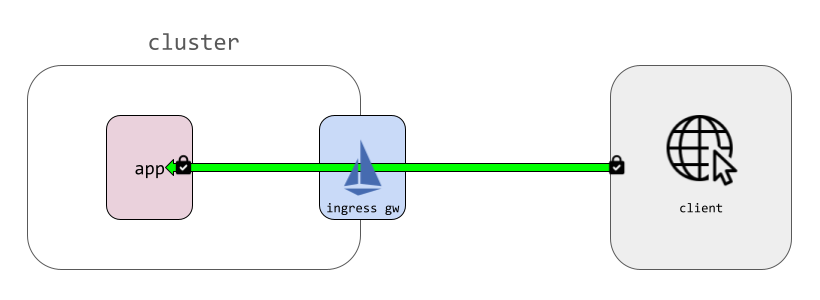
If a client outside the mesh makes a request to https://yourcompany.com/ and you have configured Istio to route TLS straight through to be terminated at your application pods, Istio cannot look inside that traffic either.
Istio Does HTTP
Istio can do all sorts of useful things with HTTP traffic. It can make routing decisions based on request properties like hostname (or authority as it’s known in HTTP2), header values, query parameters, and so on. It can produce fine grained metrics and logs capturing details like request counts and HTTP and gRPC status codes. And it can enforce traffic policies, allowing or rejecting requests based on attributes like the HTTP method, or the claims present in a JWT, or the URI being accessed.
However in order to do these things it has to be able to inspect the traffic.
Istio Does TLS
Istio can also do useful things with TLS traffic. It can route requests based on SNI headers, observe the number of bytes sent and received, and the number of active connections. But, Istio cannot look inside TLS encrypted traffic 1 yet 2.
Footnotes
Unless you have the key & cert for the target domain, or generate a self signed cert and configure Istio to trust it.↩︎
Work is underway to implement squid proxy style “TLS bumping” in envoy. See this github issue and this istiocon presentation for more info.↩︎